Cybersecurity Competency Services
In today’s fast-moving business environments, the cybersecurity threat and risk landscape continue to expand and evolve.
At NTSS, we assess cybersecurity risk posture not only by reviewing technology, but also people and business processes; what they do, how they do it and who does it!.
Vulnerability Assessment & Penetration Testing
Identify and react to threats to your organization with a vulnerability assessment & penetration testing.
NTSS works with organizations to deliver internal and external network vulnerability assessments, penetration testing and firewall assessments to ensure there are no gaps in your infrastructural defenses.
Security Awareness Training
Our Security Awareness approach starts with your people—protecting and empowering them through
education and simulated cybersecurity attacks.
Network Security Assessments
Our objective is to ensure that the necessary security measures are implemented and integrated into your network infrastructure. Through our industry proven security assessment methodology, we will provide you with a comprehensive report, outlining existing vulnerabilities and develop actionable recommendations to resolve the security issues at hand.
Physical Security Assessments
A Physical Security Assessment provides an independent verification of the organizational security measures implemented to protect its employees, assets and sensitive data. Verification of compliance policies implemented, security controls, identification of gaps, evaluation of risks, and prioritized remediation reports.
Cybersecurity maturity assessments
Have clients, partners or stakeholders asked about your security controls, or how your organization stacks up against security standards? NTSS helps determine which standard your organization should be measured against, depending on factors such as industry, size and client base. Whether it is ISO 27001/27017/27018, NIST
Cybersecurity Framework, CIS Critical Security Controls, SSAE 18 (SOC 1 and SOC 2) or PCI DSS, we help you on this journey. We also provide a maturity rating to determine which areas of your security program needs attention.
Data Protection / Privacy impact assessments
Does your organization store, process or transmit personally identifiable information (PII) or have to comply with GDPR? NTSS conducts a privacy impact assessment to determine privacy risks and impact to your organization. We help determine where your data resides, how critical it is and what you need to do to protect that data. At the end of the assessment, we provide you with recommendations and a privacy roadmap to help outline the necessary actions you must take to protect your organization.
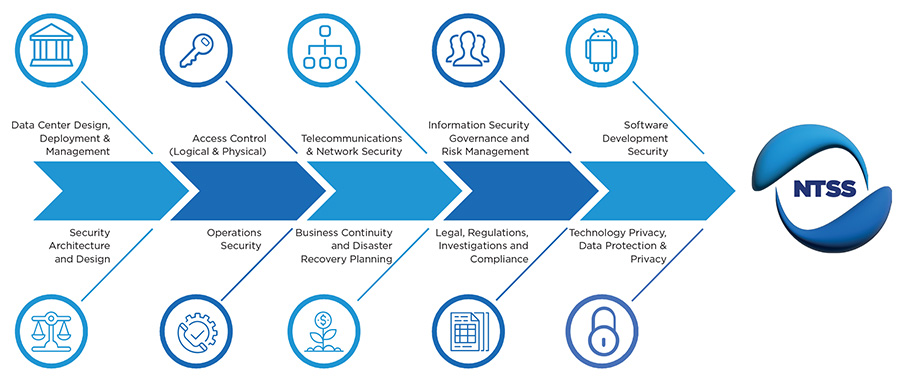
Cybersecurity program design and implementation
We help organizations design and implement fit-for-purpose cybersecurity programs that take into consideration the ‘crown-jewels’ and other assets of the organization and their criticality to the organization.
Information Security Governance and Risk Management
We help organizations navigate the difficult path of setting up an information security governance capability as part of the requirements for the implementation of an Information Security Management System to provide the necessary guidance and direction for the organization with the associated risk management controls.
Data Center design, deployment and management
We comply with industry standards and work with organizations to design and build data centers to suite and complement their requirements. The principles of our design approach are based on simple, scalable but highly efficient technologies that deliver real value through the lifecycle of the facility. We ensure the infrastructure we design operate seamlessly with no disruption to services or business continuity.
Our standards are world class and our designs are based on the client’s business plan and growth forecast.
Training & Certification
With certified trainers as part of our core team, NTSS has the capacity to provide training in selected ISO frameworks (ISO 27001 LA/LI etc) and other cybersecurity industry certifications.
ISO Standards Implementation
Our ISO Certified Trainers provide the needed training, guidance and handholding to organizations that seek ISO 27001 Certification as part of their regulatory and fiduciary requirements.
